Blog
April 28, 2023
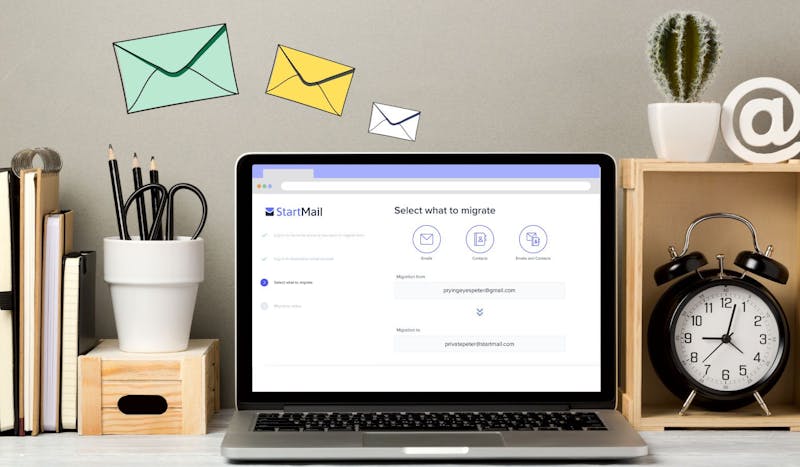
Switch to Secure Email – Migrate Easily! | Private & Encrypted
Migrating to StartMail is simple – Enjoy encrypted, ad-free email with no tracking – Secure your inbox and switch today!

March 15, 2023
Protect Your Privacy as a Consumer – Top Tips
Learn to safeguard your personal information with privacy products, limiting data sharing, understanding privacy policies, and shopping safely online.

March 3, 2023
Enhance Your Password Security – 5 Essential Tips
Discover five tips to improve password management, including strong policies, password managers, and multi-factor authentication to protect your accounts.
February 28, 2023
Use Email Aliases to Stay Private – Protect Your Inbox!
Learn how to protect your privacy with email aliases – Reduce spam, hide your real address, and stay in control of your inbox.

January 26, 2023
Startling Email Privacy Facts – What You Need to Know
Uncover eye-opening email privacy facts – Learn how your data is tracked and how StartMail keeps your emails private – Take back your online privacy today!

January 6, 2023
Protect Your Data in the New Year – 5 Key Tips
Discover five steps to keep your data safe in the new year, including password management, two-factor authentication, and using a secure email provider.

December 19, 2022
5 Best Privacy Gifts – Keep Your Data Safe & Secure
Looking for the perfect privacy gift? Discover 5 great gifts for tech enthusiasts, security-conscious users, and anyone who values online privacy.

November 21, 2022
10 Tips | Safe Online Shopping – Protect Yourself, Avoid Scams
Shop online with confidence – Learn 10 essential tips to protect your privacy, secure payments, and avoid scams. Stay safe while shopping!

October 27, 2022
4 Email Hacking Horror Stories to Haunt You This Halloween
Read about four real email hacks and discover five essential tips to secure your email account against cyberattacks.

October 6, 2022
Why You Should Protect Your Emails – Keep Your Data Safe
Discover four compelling reasons to safeguard your emails: protect privacy, secure data, prevent unauthorized access, and avoid phishing scams.